Cybersecurity threats are a growing concern in the healthcare industry, where patient information is a goldmine for criminals. But what are the specific tactics they use? And more importantly, how can your practice defend itself? This blog explores the top 5 cybersecurity threats facing healthcare providers and offers practical solutions to mitigate them.
1. Phishing Attacks:
- Description: Phishing attacks are a form of social engineering where cyber criminals attempt to trick individuals into revealing sensitive information, such as login credentials, credit card details, or Social Security numbers. They typically achieve this by impersonating a trusted entity (like a bank, healthcare provider, or a trusted platform) through deceptive emails, text messages, or even phone calls. These messages often create a sense of urgency or fear, pressuring the victim to click on a malicious link or download an attachment.
- Example: In 2021, a widespread phishing campaign targeted Microsoft Office 365 users. Attackers sent emails disguised as legitimate notifications from Microsoft, claiming there were issues with the recipient's mailbox. The emails contained a link that, when clicked, directed users to a fake login page designed to steal their Microsoft credentials. This attack was particularly successful because it mimicked the design and language of real Microsoft notifications.
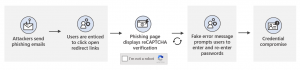 Source: https://www.microsoft.com/en-us/security/blog/2021/08/26/widespread-credential-phishing-campaign-abuses-open-redirector-links/
Source: https://www.microsoft.com/en-us/security/blog/2021/08/26/widespread-credential-phishing-campaign-abuses-open-redirector-links/ - How Phishing Attacks Work:Phishing attacks can be very sophisticated and often rely on a combination of tactics to deceive victims. Here's a breakdown of how they typically work:
- Impersonation: Attackers pose as a trusted source. They may use logos, familiar language, and even spoofed email addresses to create a sense of legitimacy.
- Urgency or Fear: Phishing emails often create a sense of urgency or fear to pressure the victim into clicking a link or downloading an attachment. Common tactics include claiming there's suspicious activity on an account, a problem with a payment, or the need to verify information urgently.
- Malicious Links or Attachments: Clicking a link in a phishing email can redirect the victim to a fake login page designed to steal their credentials. Downloading an attachment might install malware on the victim's device, which can steal data, spy on activity, or hold data hostage (ransomware).
- Mitigation:
- Implement staff training programs on phishing awareness. Train staff to be suspicious of unsolicited emails, to verify sender addresses, and to hover over links before clicking to see the true destination URL.
- Utilize multi-factor authentication (MFA) which requires a second verification step beyond a password, like a code sent to a phone, to log in.
- Implement email filtering solutions that can identify and block phishing attempts.
- Have your IT provider send fake phishing campaigns to your staff - if anyone clicks or submits data - this is a great opportunity to train them.
- Have your IT provider add (in large unmistakable letters) EXTERNAL SENDER to emails that originate outside your organization.
2. Ransomware:
- Description: Ransomware is a type of malicious software (malware) specifically designed to encrypt a victim's data, rendering it inaccessible. Hackers then demand a ransom payment, typically in cryptocurrency, to unlock the data. Ransomware attacks can be devastating, especially for healthcare organizations. By encrypting patient medical records, appointment scheduling systems, and administrative data, ransomware can cripple an organization's ability to function. This can delay critical treatments, endanger patient safety, and cause significant financial losses.
- Example: In February 2024, a cyberattack targeted Change Healthcare, a major healthcare technology vendor. The attack disrupted critical services like claims processing, eligibility verification, and appointment scheduling for many healthcare providers across the country. While Change Healthcare is a large company, the attack significantly impacted smaller practices that relied on its services. This incident highlights the cascading effect of cyberattacks on the healthcare ecosystem and the importance of robust cybersecurity measures throughout the industry.
- How Smaller Practices Are Vulnerable: The Change Healthcare attack demonstrates how even an attack targeting a third-party vendor can disrupt operations for smaller healthcare providers. Smaller practices may not have the resources or expertise to implement the same level of cybersecurity as larger organizations, making them more susceptible to the downstream effects of cyberattacks.
- Mitigation:
- Regularly back up your data securely and ensure there is a copy of backups that are isolated from your network. This way, you can restore your data from backups if attacked without paying the ransom.
- Continuous network monitoring to detect suspicious activity and potential breaches before they occur.
- Automated security patch management to ensure your systems are always up-to-date and protected against vulnerabilities.
- Ongoing security awareness training to empower your staff to become the first line of defense against cyber threats.
- Disaster recovery planning to help you quickly restore critical systems in case of a cyberattack.
- Cyber Liability Insurance is important, but be sure to speak to experts to ensure you are properly covered.
3. Uncontrolled Physical Access and Weak Access Controls:
Description: In the healthcare industry, where patient privacy is paramount, controlling physical access to devices and network infrastructure is crucial. Unsecured entry points, weak passwords, and lax access control policies can create significant vulnerabilities for cybercriminals to exploit. The HIPAA Security Rule mandates that covered entities implement physical safeguards to protect electronic protected health information (ePHI).
HIPAA Requirements: The HIPAA Security Rule requires covered entities to implement "administrative, physical, and technical safeguards" to ensure the confidentiality, integrity, and security of ePHI. The physical safeguards section specifically addresses access control to ensure only authorized personnel can access ePHI. This includes controlling physical access to devices and workstations that store or transmit ePHI, as well as implementing a process for terminating access when an employee leaves the organization.
Security Risks of Uncontrolled Access:
-
Physical Theft: Unrestricted physical access to devices like laptops or servers storing ePHI can lead to outright theft of the equipment. This can result in a significant data breach, compromising patient privacy and potentially causing financial losses for the healthcare provider.
-
Unauthorized Access and Insider Threats: Weak access controls, such as lax password policies or granting excessive access privileges, can create opportunities for unauthorized individuals (including disgruntled employees) to gain access to ePHI. This can be done through various means, such as social engineering tactics to trick employees into revealing credentials or exploiting weak passwords.
Mitigation Strategies:
- Implement a layered security approach: This includes securing physical access points to buildings and server rooms, requiring strong authentication protocols (e.g., multi-factor authentication), and enforcing the principle of least privilege (granting access only to the data necessary for specific job functions).
- Regularly review and update access control policies: Regularly evaluate access needs and revoke access privileges for terminated employees or those whose roles no longer require access to certain data.
- Employee Training: Educate staff on the importance of physical security measures, password hygiene, and how to identify and report suspicious activity.
4. Data Breaches:
-
Description: Data loss and exfiltration occur when sensitive patient information (PHI) exits a healthcare organization's authorized channels. This can happen intentionally through malicious cyberattacks, unintentionally through human error, or through physical theft of devices.
Data Loss Methods:
- Cyberattacks: Hackers can employ various techniques to infiltrate a network and steal PHI. This could involve exploiting vulnerabilities in software, social engineering tactics to trick employees into revealing credentials, or deploying malware to steal data.
- Physical Theft: Unsecured devices like laptops, smartphones, or USB drives containing PHI can be stolen, leading to a data breach.
- Human Error: Accidental data loss can occur through mistakes like emailing PHI to the wrong recipient, misplacing devices containing unencrypted data, or improper disposal of sensitive documents.
Example: A doctor accidentally emails a patient's medical records to the wrong address. This could expose the patient's sensitive information to a stranger and violate HIPAA regulations.
HIPAA and Data Loss Prevention: The HIPAA Privacy Rule requires covered entities to implement safeguards to protect the confidentiality of PHI. This includes measures to prevent unauthorized access, use, disclosure, or disposal of ePHI. Data loss prevention (DLP) solutions can be a valuable tool in achieving these goals.
Mitigation Strategies:
- Data Encryption: Encrypting data at rest (stored on a device) and in transit (being transmitted over a network) scrambles the information, rendering it useless without a decryption key. This significantly reduces the risk of a data breach even if unauthorized individuals gain access to the data.
- Data Loss Prevention (DLP): DLP solutions can monitor and control the flow of data across your network. They can help prevent unauthorized data transfers by blocking emails containing sensitive information or restricting the use of unauthorized USB drives.
- Employee Training: Regular training for staff on data security best practices is crucial. This includes educating employees on how to identify and avoid phishing attempts, the importance of strong password hygiene, and proper handling of sensitive information.
5. Insider Threats
Description: Insider threats arise from malicious or negligent actions by individuals with authorized access to a healthcare organization's systems and data. These threats can be intentional, such as a disgruntled employee stealing patient data, or unintentional, due to lax security practices by authorized personnel.
Insider Threat Risks:
- Data Theft: Authorized users may steal patient data for personal gain or sell it on the black market. Insider knowledge of an organization's security protocols can make them difficult to detect.
- System Sabotage: Disgruntled or careless employees may deliberately damage or disrupt critical healthcare systems, potentially impacting patient care and causing financial losses.
- Selling Access: Insiders may sell their access privileges to cybercriminals, allowing them to infiltrate the network and launch more sophisticated attacks.
Example: A healthcare employee with access to patient billing information uses that data to commit medical identity theft.
HIPAA and Insider Threats: The HIPAA Security Rule requires covered entities to implement policies and procedures to address the risks associated with workforce access. This includes conducting a risk assessment, implementing access controls, and providing security awareness training for employees.
Mitigation Strategies:
- Background Checks: Conduct thorough background checks on new hires, especially those with access to sensitive data.
- Least Privilege Access Control: Grant employees access only to the data and systems they need to perform their job duties (principle of least privilege). Regularly review and update access privileges to ensure they remain appropriate.
- Security Awareness Training: Regularly train employees on cybersecurity best practices, including data security protocols, password hygiene, and how to identify and report suspicious activity.
- Termination Procedures: Implement clear procedures for terminating employee access to systems and data when their employment ends.
Conclusion: Protecting Your Patients' Data Starts Now
The healthcare industry faces a constant barrage of cybersecurity threats. From weak access controls to insider threats, these vulnerabilities can have a devastating impact on patient privacy and your practice's reputation.
By understanding these top cybersecurity threats and implementing the mitigation strategies outlined in this blog, you can significantly improve your defenses. Remember, even small practices are targets, and taking action is crucial.
Don't wait for a breach to happen before taking action.
At Integrated Technology Group (ITG), we understand the unique challenges faced by healthcare providers in Virginia. Our team of HIPAA and cybersecurity experts can help you develop a comprehensive security strategy tailored to your specific needs. We offer a range of services, including:
- Vulnerability assessments and penetration testing to identify and address weaknesses in your systems.
- Implementation of robust access controls to ensure only authorized personnel have access to sensitive data.
- Data encryption solutions to protect patient information at rest and in transit.
- Ongoing security awareness training for your staff to become the first line of defense against cyber threats.
Contact ITG today and let our team of experts help you safeguard your patients' data and ensure your practice remains HIPAA compliant.
Together, we can build a more secure healthcare ecosystem for everyone.